eKYC or e-KYC is short for “electronic know your customer”. In our digital-first world, eKYC is how banks, fintechs, and financial institutions onboard their customers while conducting identity verification to stay compliant with regulations.
Electronic identification (eID) combines both active and passive signals for customer verification, utilizing tools such as facial recognition technology and image recognition for id verification to establish the customer's identity during digital onboarding.
If deployed correctly, eKYC ensures a compliant, yet paperless process for your customers. Additionally, the process allows companies to do a proper risk assessment while satisfying customer due diligence needs and protecting their business from fraud.
While that might sound good on paper, and technically you can choose between many different eKYC solution providers, the verification process can still make a dent in your bottom line in the form of hidden costs.
Simply put, no matter which provider you work with, if you make mistakes during the design of your onboarding process, customers will get frustrated and churn.
In this article, we will explain what eKYC processes are, what kind of signals they operate with, and how to implement digital verification correctly.
How do eKYC processes work?
An eKYC process involves several steps. First, whenever a new user signs up for a service, they must provide personal details such as their name, address, phone number, and email address.
Then, they must upload copies of ID documents such as passports, drivers licenses, and national IDs. The uploaded information is then compared to various databases such as government records, credit agencies, and other public records to corroborate the user's identity.
Once the user's identity is verified, the service provider can review the user's account information to ensure that all necessary details have been provided.
If the information provided by the user does not match with the records, the approval can be denied, or the user can be asked to reapply with correct or additional information.
The viability of eKYC technology has improved tremendously over the past decade as now virtually everyone has a smartphone in their pocket with a high quality camera that makes the process as smooth as taking a selfie.
This has led to the proliferation of self-service KYC flows, where users are guided through the process by service providers with virtually no human oversight.
Other financial institutions, however, have found success in what's known as customer experience management - having an agent available who guides the user through the process live, during a video call. This doubles as a form of video identification, which also protects you from some common forms of fraud that might pass the barriers in a more hands-off process.
The approach you take depends on the kind of clientele you are serving and how tech-savvy they are, as well as how much you need to optimize for costs.
The point is to allow your customers instant access to your services in order to minimize churn as much as possible while fulfilling your KYC obligations.
To do so without granting entry to potentially malicious actors, you need to tap into the full advantages granted by eKYC by using:
Active signals
Third party data
And passive data
Let’s have a look at how you can combine the three approaches during your eKYC process.
Different signals used to establish customer identity
Traditionally, KYC relies on document verification to establish that the client is indeed who they say they are.
This means when you ask for the customer's personally identifiable information, such as their name, address, date of birth, SSN, passport number, or driver's license, you also ask for them to submit these documents.
These are called active signals.
Active signals for document verification
While traditionally document verification would mean scanning the documents in question, the abundance of smartphones and image recognition technology allows eKYC providers to verify personal identification documents using photos taken with their camera.
Alternatively, if you rely on video KYC, you can ask your customers to present identity documents during onboarding.
It's worth noting that many governments are now providing eIDs to their citizens. The most notable example would be Aadhaar in India:

When it comes to providing loans to your clients, you would also ask them for proof of their source of income.
In Europe, thanks to Open Banking initiatives, you can increasingly rely on banking APIs to verify the income of applicants by accessing their financial information directly, rather than asking for bank statements, making the process even more seamless than ever before.
Hopefully, this revolutionary change in financial technology will soon be a reality in the US as well, where legislators are still finalizing the details to best serve the interests of consumers.
In the meanwhile, third-party data providers help automate the lending process by verifying the income and employment information of the applicants.
It is important to note, however, active signals alone are not enough to verify a customer’s identity.
Instead, you need to combine active signals with third-party data providers and passive signals. By doing so, you’ll fulfill your anti-money laundering (AML) duties and ensure you are protecting your business against identity fraud.
Third-party data: what's your reputation?
Third-party data in the eKYC context refers to cross-referencing the information provided by the applicant with external databases, sources, or service providers.
When it comes to AML, you would traditionally check the customer's information against the following external databases:
Government watchlists & sanction lists
Politically exposed persons (PEP) lists & adverse media reports
Email & phone number reputation services
In fact, by prioritizing these checks in your decision flow over the more costly document verification processes, you can lock out bad actors while approving good ones and saving money.
The problem with third-party data is that different databases will store and provide information about the same entity in different formats. For example, think of a customer who shortens their middle name, or someone whose name can be spelled differently in different languages.
The solution to third-party data issues is called entity resolution. Your KYC process should account for such data discrepancies and correct them automatically, establishing whether or not the different entities you face are connected or not.
At Oscilar, for example, we have over 100+ integration partners available out of the box to give you a 360-degree view of your customers. The platform was designed to address some of the most common challenges risk teams face on a daily basis when it comes to using different software solutions, and their complex operations. Our entity resolution supports multiple data types, ingesting and processing data from a variety of sources, including structured, semi-structured, and unstructured data in order to support our robust entity link analysis features to help decision makers.
If you are curious about how Oscilar can serve as an eKYC platform, take a minute to watch our demo.
Once you have your active signals paired up with third-party sources, you still have to consider passive data: information you can infer about your user based on their device, connection, and behavior.
Passive signals: the first line of defense
Passive signals during eKYC refer to the bread and butter of anti-fraud and risk assessment measures. They help you assign a risk score to the user by analyzing their device and connection to establish a baseline of who they are.
Digital devices provide a wealth of information that can be used to determine if we're legit. For example, the following is a list of data points easily gathered from digital devices:
IP Address: The user IP can reveal their location, which can be checked against their address, but it can also be checked to see if they are connecting via proxies or VPNs, trying to conceal their true location.
Device and browser fingerprints: These provide handy details that can point to discrepancies. Are the language and timezone settings correct? Does the machine fit what you would expect from your target market? Are there multiple users coming from the same device with no good reason? Device fingerprinting technology allows you to gather information directly from the user’s device, and use those data points to uncover connections between users, or to uncover hidden truths.
Cookies and other metadata: Again, this is something you can use to establish connections between the user you are seeing now and entities you might have encountered in the past. By utilizing browser cookies, you can easily identify returning visitors, allowing you to compare information they presented in a previous session with what they’re providing you now.
Passive signals should be your first line of defense. By running risk analysis on them before triggering any other KYC processes can save you a lot of money and headaches.
You can be creative when it comes to collecting them too: email verification links for example might be clicked from a different device than the one the user is using for their application, and passive signals can reveal glaring discrepancies, for example, if you are dealing with a fraudster who has set up their VPN on the computer, but uses their home WiFi address on their mobile.
In addition, passive signals can be used as signs of confidence: you can increase user satisfaction if you remember the device details they used at signup during later interactions, and give them the benefit of the doubt even if they are accessing the service from a different location.
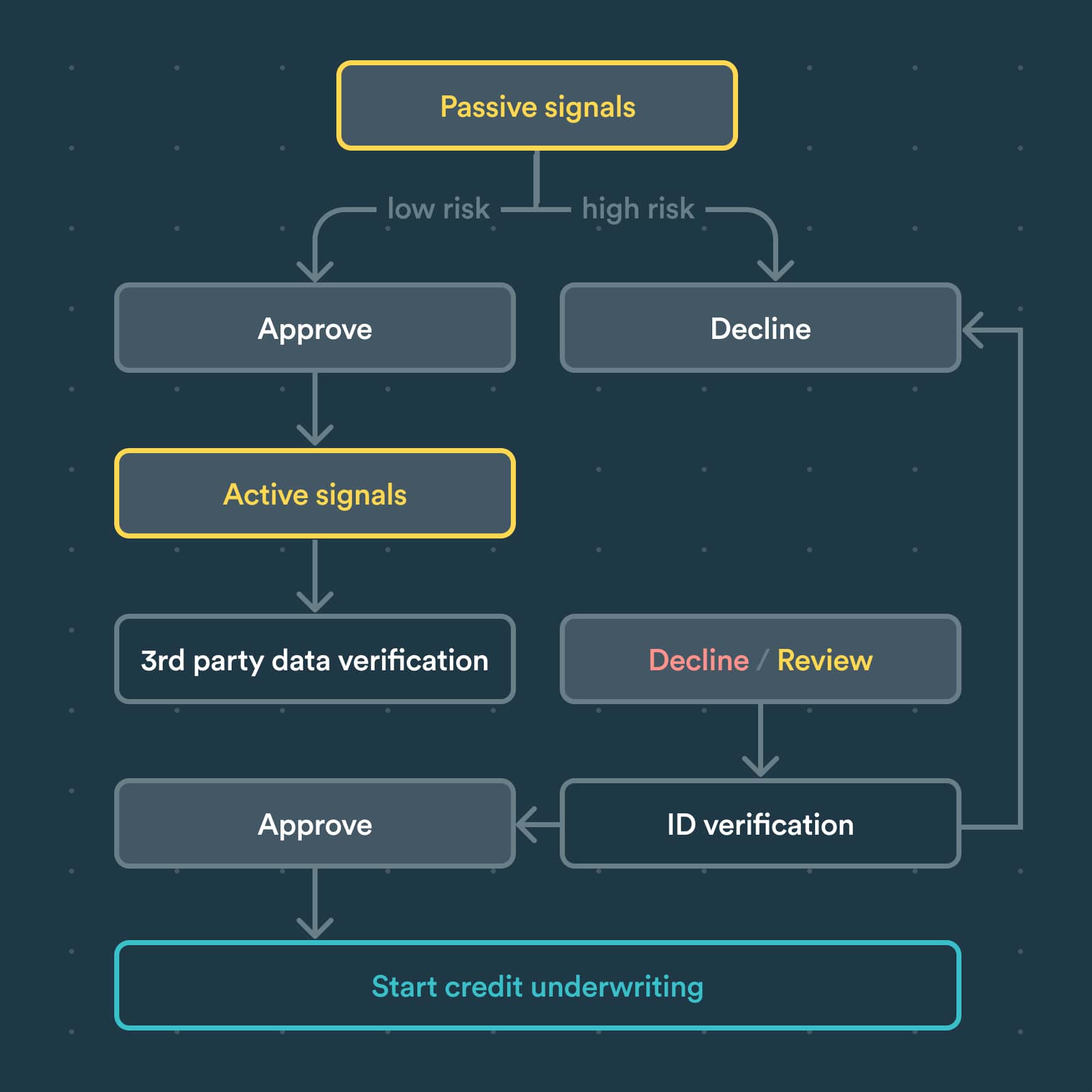
Putting it all together: the eKYC decisioning flow
There is no one size fits all approach for handling eKYC. The providers you choose and the processes that you implement will depend on a myriad of factors beyond regulatory obligations.
Ideally, your risk team should have full control of the process, with the autonomy to swiftly switch if something isn't working as intended. They should be able to experiment and deploy decisioning flows in different markets, as well as tailor your risk rules based on quickly changing circumstances.
Here are a couple of things to remember when designing your eKYC guidelines and decisioning flow:
Start with passive signals. No need to waste resources on users with ill intentions. Passive signals allow you to filter out bad users before triggering more expensive KYC checks.
Keep user friction in mind when establishing trust. Layer your verification process so it's not obtrusive to your users while still maintaining kyc compliance.
Ongoing monitoring of effectiveness & costs. Many companies just 'tick the box' when it comes to eKYC verification. In this day and age, you can do more: don't be afraid to experiment with multiple providers and different decisioning flows to see if you can increase your approval rate without an additional increase in fraud or risk.
Coherent entity, data, and case management. Your eKYC providers can only get you as far as your internal tooling and systems allow them. It's crucial that your case management system is not only able to handle in-house and third-party data, but that it allows your risk teams to act on that data - not just on a case-by-case basis, but at scale.
With these in mind, you can provide a great customer onboarding experience without straining your resources and expenditures on the operation side.
The ekyc process should be used to your advantage and not treated as a burden.
Identity verification & digital account opening
In summary, while KYC regulations are constantly evolving, you have a lot to gain by carefully considering how you implement your digital KYC and verification processes.
Customers are increasingly fickle, and your regulatory need for detailed information should not weigh down your digital onboarding process.
With a lot of eKYC solutions to choose from, at the end of the day, your success comes down to how you implement different measures, trigger electronic identification steps and allow or block) your users from proceeding.
In order to do that, you need to empower your risk operations team with a tool that gives them not just the relevant data (be it active, third-party or passive), but the proper autonomy to act on it as well.
If you are curious about such a solution, consider booking a demo to see Oscilar in action below and get started with over 100+ integration partners, customizable decisioning flows, and entity resolution right out of the box.